New IBM Network Security Appliance Launched
Updated: 2012-07-31 07:41:22
IBM announced the availability of a new network security appliance, the IBM Security Network Intrusion Prevention System. - IBM has announced a new class of network security appliance that delivers a more granular view of an organizations IT security and delivers a simplified security management interface.
The IBM appliance helps enterprises control new risks posed by social media and web browsing, IBM said. The new ne...

 It’s been a very busy July here at BeyondTrust, especially the last two weeks! We’ve just returned from the annual BlackHat conference, where we had tremendous response to demonstrations of our Context Aware Security Intelligence solutions. BlackHat, as many of you know, is the industry’s most well respected technical security conference, so we were very [...]
It’s been a very busy July here at BeyondTrust, especially the last two weeks! We’ve just returned from the annual BlackHat conference, where we had tremendous response to demonstrations of our Context Aware Security Intelligence solutions. BlackHat, as many of you know, is the industry’s most well respected technical security conference, so we were very [...] Veracode’s remedy for the Application Security headache is in full swing at the Black Hat Conference. Swing by the booth (#229) and you can pick up an “I See our picks!
Veracode’s remedy for the Application Security headache is in full swing at the Black Hat Conference. Swing by the booth (#229) and you can pick up an “I See our picks! This article provideds an overview of what SCM v. 2.5.40 does and how it does it.
This article provideds an overview of what SCM v. 2.5.40 does and how it does it. Have you ever wanted to root your Android device, so you could be like all the other cool kids on the block? If you did your research, you learned that it makes it easier for attackers to keep their malware on your device, if it were to be infected, through the use of a rootkit. [...]
Have you ever wanted to root your Android device, so you could be like all the other cool kids on the block? If you did your research, you learned that it makes it easier for attackers to keep their malware on your device, if it were to be infected, through the use of a rootkit. [...] Metasploit was recently updated with a module to generate a wpad.dat file for WPAD man-in-the-middle (MITM) attacks. This blog post explains how this attack works and how to investigate such an attack by analyzing captured network traffic. Windows' WPAD feature has for many years provided attackers[...]
Metasploit was recently updated with a module to generate a wpad.dat file for WPAD man-in-the-middle (MITM) attacks. This blog post explains how this attack works and how to investigate such an attack by analyzing captured network traffic. Windows' WPAD feature has for many years provided attackers[...] Secure coding is a challenge that every software company in the world faces. Even the largest companies that attract the best developers in the world (Read: Google, Facebook) have multiple instances of vulnerabilities in their code ranging from XSS to SQL injection to backdoors. So how can you integrate security into your SDLC?
Secure coding is a challenge that every software company in the world faces. Even the largest companies that attract the best developers in the world (Read: Google, Facebook) have multiple instances of vulnerabilities in their code ranging from XSS to SQL injection to backdoors. So how can you integrate security into your SDLC?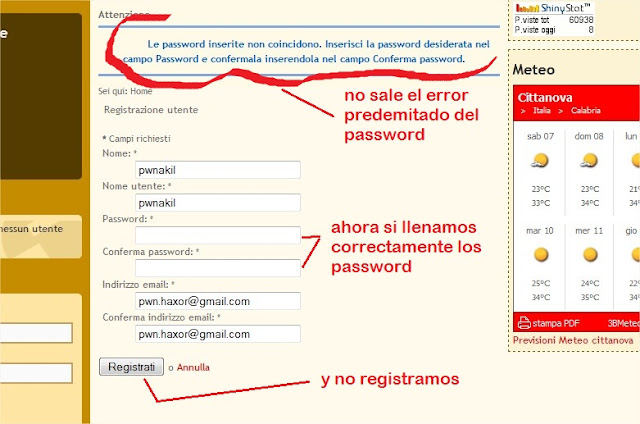 <p
<p
 </a
</a
 In this multi-part series, we'll take a look at what's new (and what's not) in security for Windows Server 2012.
In this multi-part series, we'll take a look at what's new (and what's not) in security for Windows Server 2012.